Cisco Secure Network Analytics, formerly Stealthwatch, is one of the most extensive visibility and network traffic analysis (NTA) / network detection and response (NDR) solutions which uses enterprise telemetry from the existing network infrastructure.
Using entity modeling and multi-layer machine learning it delivers advanced threat detection, speedy threat response, and simplified network segmentation. Along with this, it will also tell you who is on your network and what exactly they are doing using advanced behavioral analytics.
Cisco’s Stealthwatch is a single, agentless solution that brings about visibility across your extended network, from on-premises to the cloud. Further, for encrypted traffic analytics, this is the only solution that helps detect malware in the encrypted traffic and ensures policy compliance without any decryption involved.
Why Stealthwatch as an NTA tool?
One of the research from the Enterprise Strategy Group, states that 87% of the organizations use NTA tools for threat detection and response today, while 43% revealed that their ‘first line of defense in an attack case is NTA.
One of the main reasons for the adoption of NTA tools is due to the ever-increasing IT complexity, like rising in multi-cloud and hybrid deployments, expanding infrastructure, employees accessing the network from any location and any device, and an increasingly large number of smart devices (OT/IoT) joining the network.
Simultaneously this increment has also shown an increase in the overall attack landscape tech usage, like, threats hidden in encrypted traffic, use of stolen credentials, rise in nation-state attacks, and much more.
While there are many players for NTA in the market, Cisco Stealthwatch has been in the market for more than 17 years and is leading the market due to the following functional strategies:
1. Multi-cloud visibility:
One needs to ensure that the security controls are being extended to the cloud while organizations increase their cloud adoption, which is ensured by Stealthwatch. It is the only network traffic analysis tool that gives truly cloud-native visibility across all the major cloud providers like Google Cloud Platform (GCP), Amazon Web Services (AWS), and Microsoft Azure.
This deployment will be agentless without having the need to install many sensors across the infrastructure. With just one solution you gain visibility across your entire network infrastructure, from cloud to on-premises.
2. Broad Dataset:
Stealthwatch always uses network metadata like NetFlow to feed into its analytics, even though many vendors feel that this way of consuming telemetry doesn’t show the complete picture and has limitations.
One of the reasons for believing these limitations is that other vendors rely on deploying a huge number of sensors and probes into the network to catch data. But this is only a trap for organizations to buy more probes and increase the workload.
Very early on, we realized that as the network expands exponentially it becomes very difficult and expensive to deploy sensors everywhere leaving many blind spots. So, we offer an agentless deployment to customers using built-in functionality in your network devices.
Further, denying the claims of relying only on Netflow, we also use contextual data from Cisco Identity Services Engine (ISE) along with tucking proxy, endpoint data, and web to provide complete visibility. If you do need to investigate the payload, Stealthwatch easily integrates with major packet capture solutions so that one can selectively analyze the malicious traffic showcased by Stealthwatch.
3. Layered analytical approach:
Complete visibility is a boon but it can be a curse when it starts to overwhelm your security team. The answer to effective analytics is too concise the massive dataset into a few actionable alerts. Stealthwatch uses about 100 different behavioral models to go over telemetry and identify anomalies.
These anomalies are then brought down to high-level alerts which are mapped to the kill-chain like reconnaissance, data exfiltration, command-and-control, and others. Cisco’s Network Traffic Analytics also employs machine learning which uses global threat intelligence powered by Cisco Talos and techniques such as supervised and unsupervised learning, rule mining, statistical modeling, and more. Some of the key outcomes of analytics within the solution are:
- Stealthwatch can automatically detect and classify devices along with their roles on the network so that your security scales on its own as per your increasing network.
- One of the key outcomes of Steathwatch is its ability to analyze encrypted traffic to detect threats and assure compliance without any decryption with the usage of Encrypted Traffic Analytics. With more than 80% of the web traffic being encrypted1 and more than 70% of the threats in 2020 predicted to use encryption2, this methodology is a major attack vector. It’s not possible anymore to depend on decryption-based monitoring.
- About ~6.7 trillion network sessions each day across ~80 million devices are processed by Stealthwatch in our customer environments to reduce them to a few crucial alerts. In fact, our clients consistently rate more than 90% of the alerts they see in the dashboard as helpful.
- Finally, instead of coming up with random metrics of workload reduction, we went up straight to our customers and asked how Stealthwatch helped them in their incident responses; and 77% agreed that it has helped them to reduce detection time and answer to threats from months to just a few hours.
4. Integrated platform approach:
Recently, Stealthwatch has been integrated with Cisco Threat Response (CTR). Stealthwatch sends alerts straight to CTR’s Incident Manager feature that allows users to see every alert alongside prioritized security alerts from other products such as Firepower devices.
Such incidents can then be investigated with additional context from your other threat response-enabled technologies, from a single all-in-one console, with just one click. Such a mechanism lowers the overall time needed to triage and respond to these alarms.
Stealthwatch can also be integrated with a firewall, through Cisco Defense Orchestrator for threat detection and effective policy management.
Advantages and Features of Stealthwatch:
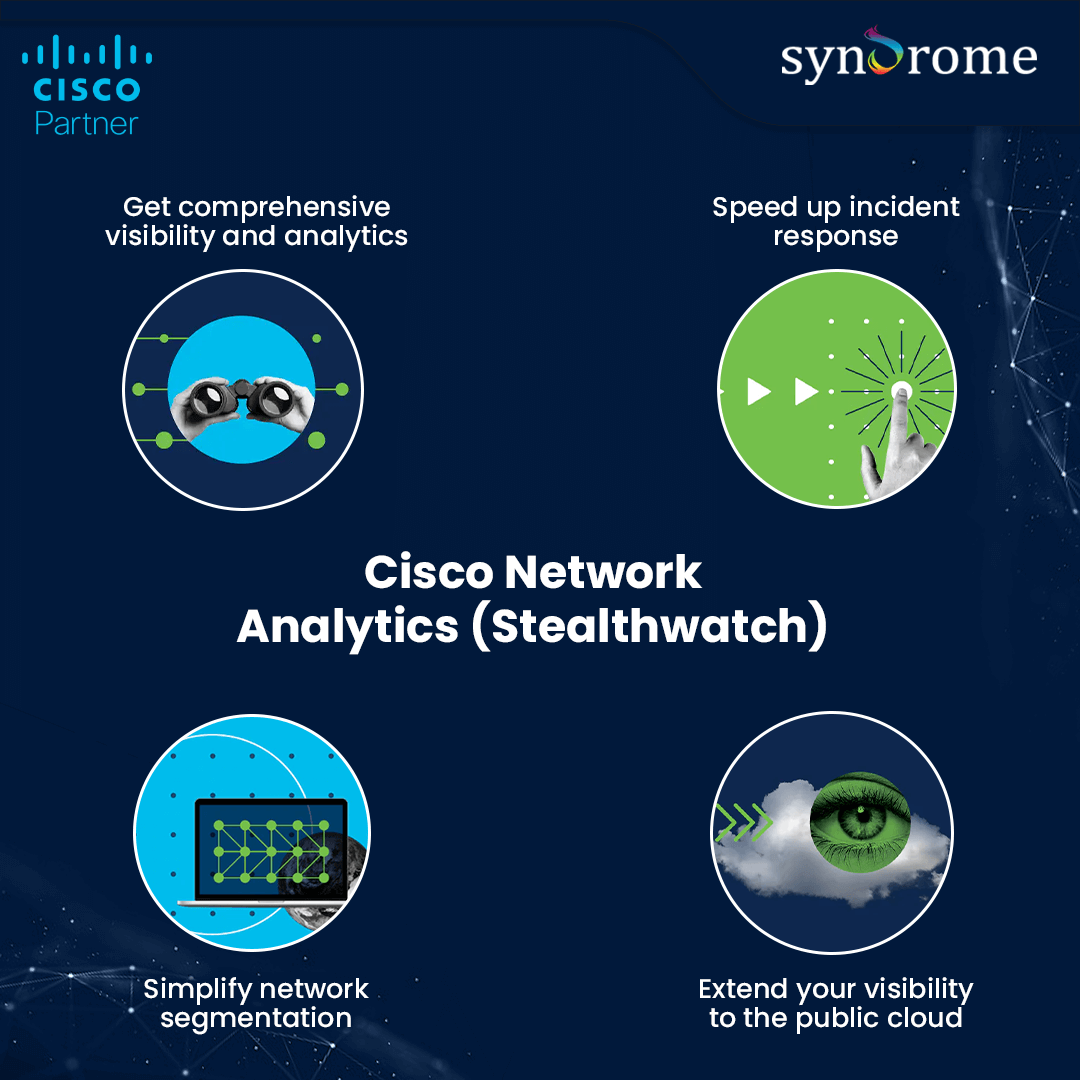
1. Extensive analytics and visibility:
Identify attacks across the dynamic network having high-fidelity alerts augmented with contexts like device, user, location, application, and timestamp. Without decryption, now analyze encrypted traffic for compliance and threats.
2. Enhance response to incidents:
Speedily identify unknown malware, insider threats such as policy violations, data exfiltration, and other sophisticated attacks with the usage of advanced analytics. For forensic analysis, store telemetry data for longer durations.
3. Simplified network segmentation:
Without any disruption to your business now define smarter segmentation policies. For detecting any unauthorized access and ensuring compliance, easily generate customs alerts. Use Secure Network Analytics with ISE to limit threats and enforce policies.
4. Outstretch your visibility to the public cloud:
With Stealthwatch Cloud, without any software agents get SaaS-based visibility and threat detection across all the major public cloud platforms.
Different convenient deployment options for Stealthwatch:
1. Secure Network Analytics:
- Hardware or virtual appliance
- On-premises data storage, SecOps, and NetOps use cases, granular tuning, air-gapped networks
- Priced by flow per second (FPS)
2. Secure Network Analytics SaaS:
- Saas based
- Simple deployment, SecOps, and light NetOps, automated tuning, also monitors Meraki and container environments
- Endpoint based pricing
3. Secure Cloud Analytics:
- SaaS-based
- Convenient for all companies using public cloud infrastructures like Microsoft Azure, Amazon Web Services, Google Cloud Platform, and server-less environments.
- Usage-based pricing supplemented by volume of log data.
Thus we can conclude, Stealthwatch helps outsmart emerging threats in your digital business with industry-leading machine learning and behavioral modeling. It helps identify who is on your network and what they are up to using telemetry from your network infrastructure, along with easily detecting advanced threats and responding to them instantly.
Protect all your important data through smarter network segmentation and all of this with an agent-less solution that expands with your business.